HTB-Netmon(writeup)
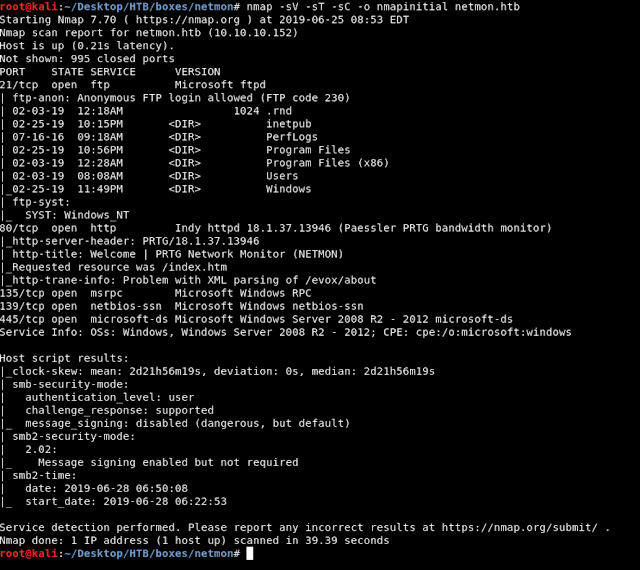
Hack The Box - Netmon Hey guys today Netmon retired and here’s my writeup on the machine. It was a easy machine that’s everything I can say about it. IP of the Box : 10.10.10.152 As always we will start with nmap to scan for open ports and services : nmap –sC –sV –A 10.10.10.152 We got ftp on port 21, http on port 80 and smb. The most interesting thing is that anonymous login is allowed on ftp. For user.txt root@kali:~/Desktop/HTB/boxes/netmon# ftp 10.10.10.152 Connected to 10.10.10.152. 220 Microsoft FTP Service Name (10.10.10.152:root): anonymous 331 Anonymous access allowed, send identity (e-mail name) as password. Password: 230 User logged in. Remote system type is Windows_NT. ftp> ls 200 PORT command successful. 125 Data connection already open; Transfer starting. 02-03-19 12:18AM 1024 .rnd 02-25-19 10:15PM <DIR> inetpub 07-16-16 09:18AM <DIR>